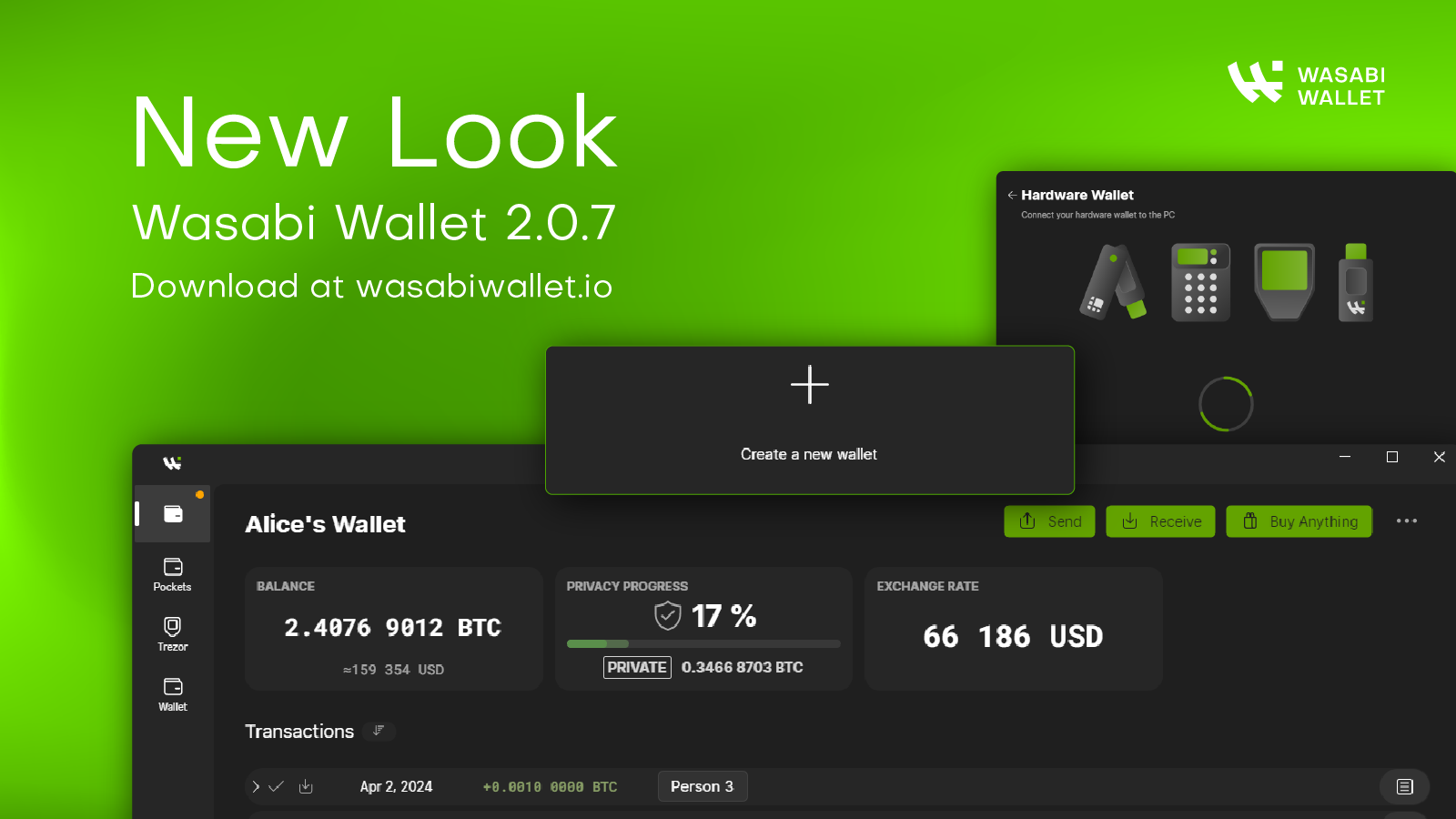
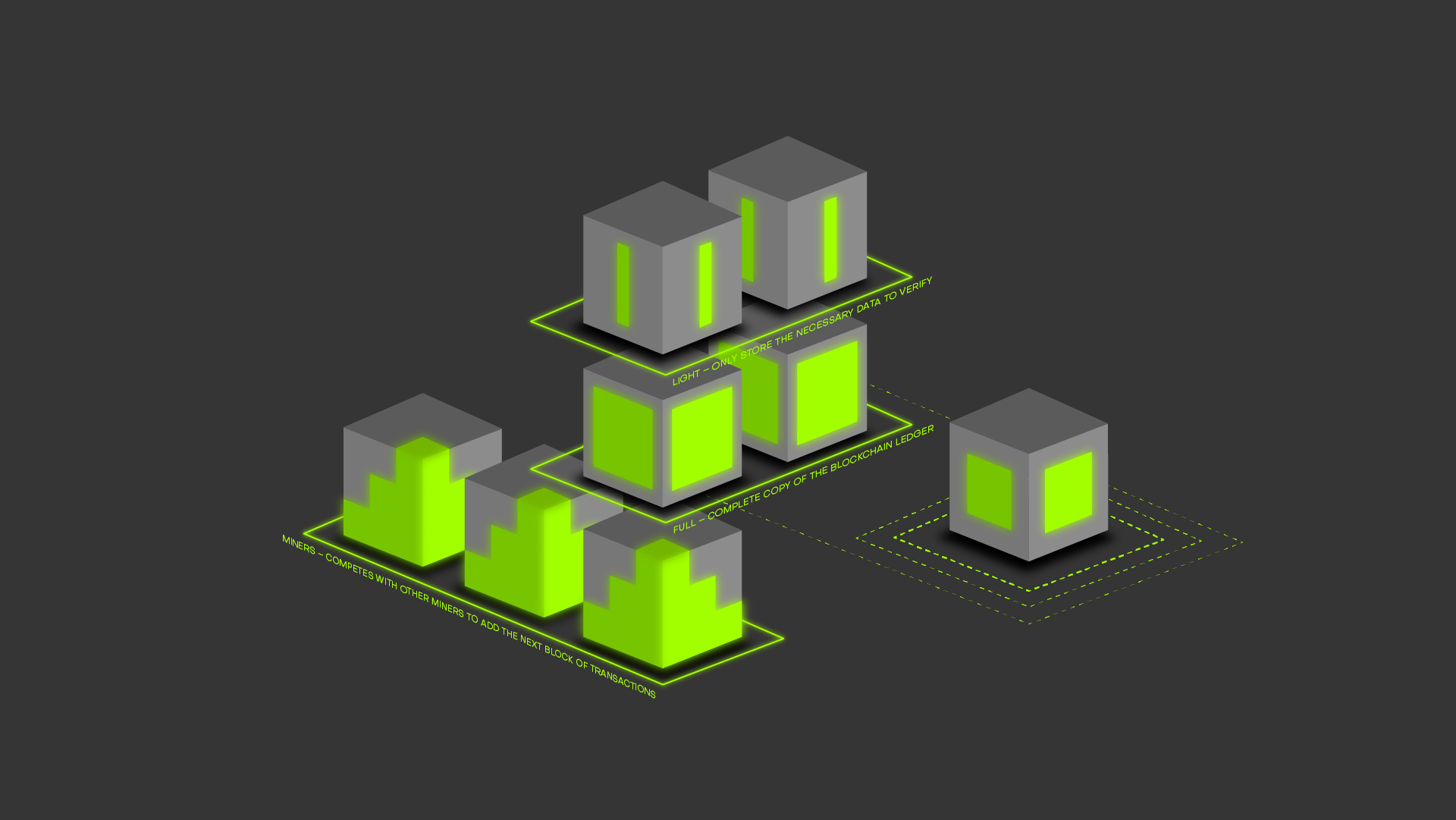
Privacy Guarantees Of Wasabi Wallet 2.0
Fully analyzing Wasabi 2.0 coinjoins is computationally hard and will probably be impossible for decades to come because a combinatorial complexity explosion is happening when we try to find all the sub-transactions of a Wasabi 2.0 coinjoin.

How Coinjoin Wallets Compare on Fees
If you want to know the details of how WabiSabi, Whirlpool and Joinmarket fee structures work, read on. We’ll define all the fees of a coinjoin transaction, the way fees are calculated for each protocol and finally, which one is better for many different user profiles.

How to Use Wasabi Wallet’s RPC Interface
The RPC is used to communicate with a running Wasabi instance. It provides some options and features which are not available (yet) when using the Graphical User Interface. Since Wasabi version 2.0.6, the RPC can be exposed as an onion service, which enables remote control.

Deeper Privacy with Safety Coinjoins
“Safety coinjoins” are triggered by default to ensure a minimum amount of remixing for users who choose to minimize costs or maximize speed. This feature anticipates how coins might be spent in the future to prevent guesses from being made based on a specific user behaviour.

Time is Money: DoS (Denial of Service) Fortification and Coinjoin Time Preference
As a result of months of hard work by the Wasabi and Tor developers, updated statistics from October 2023 show that the overall success rate has more than doubled since the previous year, with over 50% of new rounds and over 80% of blame rounds succeeding.
Friends and Plebs Don’t Pay Wasabi Coinjoin Fees
In this article, we’ll explain how Wasabi coinjoin fees work, how it differs from Wasabi Wallet 1 with Free Remixing, what Friends don’t pay means, the importance of accessibility in coinjoin transactions, what Plebs don’t pay means, why mining fees are never waived, and finally how to minimize mining fees in a high-fee environment.